Sometimes you need to do a packet capture on a Windows machine without installing anything. This is a guide on how to use the inbuilt Windows utility – netsh trace – to capture IPv4 packets. For just capturing DNS packets, capturing only UDP packets should cover most DNS traffic.
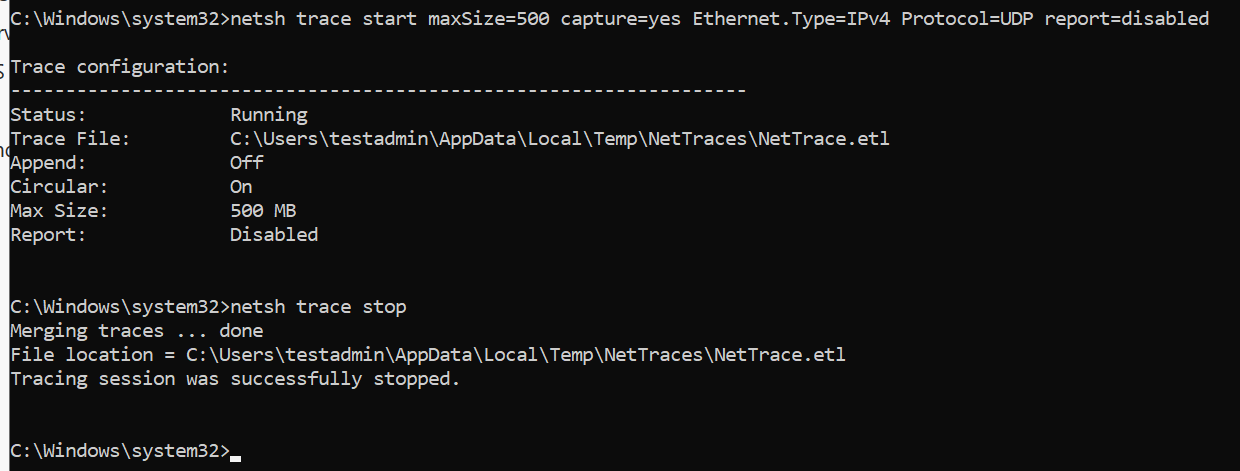
#Run this command in an elevated command prompt
netsh trace start maxSize=500 capture=yes Ethernet.Type=IPv4 Protocol=UDP report=disabled
#When you want to stop the packet capture run
netsh trace stop
For capturing all types of packets, leave out the Protocol Type:
netsh trace start maxSize=500 capture=yes Ethernet.Type=IPv4 report=disabled
Next, download etl2pcapng from Github then run the following commands to convert the .etl file to a PCAPNG.
#https://github.com/microsoft/etl2pcapng
#Convert ETL file to pcapng
.etl2pcapng.exe .NetTrace.etl nettrace.pcapng
Open the .PCAPNG file just created in Wireshark and go to File > Save As > PCAP
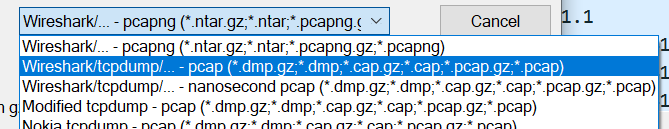
You now have a PCAP file that can be imported into Zeek for analysis in RITA